COM+ Tutorial from Scratch has two parts. Part I has basic concept of COM+ and its related topics. Part II will teach you how to use COM+ in real world applications.This article is an extended version of my previous article " What COM+ exactly is?". This tutorial explains what is COM+ and how it works in real world applications. I have used Windows 2000 and VC++ 6.0.
Windows DNA is the first steps to understand COM+.
Windows DNAWindows DNA is a framework that describes how to develop multi-tier, high performance, scalable, and distributed applications over the network. The goal of DNA is to provide enterprise level solutions which is suitable for any size. The heart of DNA is an integrated programming model based on COM+. In other words, Windows DNA is a way to provide an enterprise based solutions from Microsoft.
Windows DNA Architecture :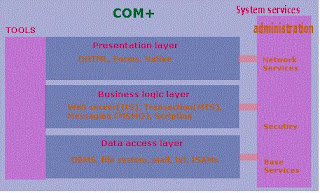 Windows DNA consists of three layers
Windows DNA consists of three layers
1. The Presentation LayerThis layer is responsible for information gathering from user, performing basic validation of user input, sending it to the business layer and again receiving results of the business layer and presenting these results to the user in a viewable formats such as VB forms. This layer consists tools such as VB, HTML, DHTML, Win32 applications, Client-Server scripting, Java Applets, Netscape Plug-Ins, ActiveX controls
2. The Business LayerThis layer is responsible for receiving input from the presentation layer, interacting with the data access layer to process the information and sending back the processed information to the presentation layer. This layer provides business rules and services to help to write scalable applications. These services are tightly integrated with each other and the underlying operating system and exposed in a unified way through COM. They include the following:
Web services, through Microsoft Internet Information Server ( IIS ).
Transaction and component services, through Microsoft Transaction Server ( MTS ).
Queuing and asynchronous services, through Microsoft Message Queue Server ( MSMQ).
Server-side scripting, via Active Server Pages (ASP).
Interoperability services, such as the COM Transaction Integrator ( COMTI ) for accessing the IBM Customer Information Control System (CICS) and IBM Infromation Management Systems (MIS).
3. The Data Access LayerThis layer directly interact with the data which usually reside in the databases such as SQL Server or Oracle. This layer is responsible for storage, retrieval, and general maintenance of data as well integrity of data. The Windows DNA approach of data access is called "Universal Data Access'. UDA is a set of system level and application level programming models called OLE-DB, ADO and RDO.
COM+: DefinitionIn 1992, Microsoft evolved OLE ( Object linking and embedding ) which was named as COM ( 1995 ) later with new enhancements and features. In 1996, COM started supporting distributing computing and Microsoft named it as DCOM ( Distributed COM). At the same time Microsoft developed one new transaction server called Microsoft Distributed Transaction Coordinator (MDTC) which was enhanced to Microsoft Transaction Server (MTS) in 1997. In 1997, Microsoft developed one more server for queuing services called Microsoft Message Queue Server ( MSMQ). Now what??? After all these development, In 1999, Microsoft combined all these services in an integrated runtime environment which is called COM+. In other words, COM+ is an integrated environment which provides developers COM, MTS, MSMQ and some other services.
